
Close





Our Antispam solution is a completely cloud-based protection that protects you against spam, phishing, scams, viruses and malware. You will also be able to have a much higher level of security for your emails sent with our email encryption.
NAT SECURITY FOR MAIL has an independent high security platform with a double scanning engine, where emails that are detected as spam, malicious or contain content that can damage the company’s information are stored, thus having a platform that takes care of the IT assets. Our platform has a secure environment that allows users to view the content of emails that have been detected as malicious or spam, without being affected regarding the company’s information.


The filtered emails will be managed, organized and eliminated by the platform administrator, as well as this management can be delegated to the users or email accounts.

NAT SECURITY FOR MAIL replicates Sandbox technology, which can study the malware that is trying to break into the organization’s internal system, analyzing and detecting attack tactics to learn from them and thus prevent future attacks. Likewise, it implements a tool with a series of solutions called DPL or Data Loss Prevention System, with the purpose of preventing the leakage of information whose origin turns out to be within the organization, performing these actions actively and without losing productivity. .

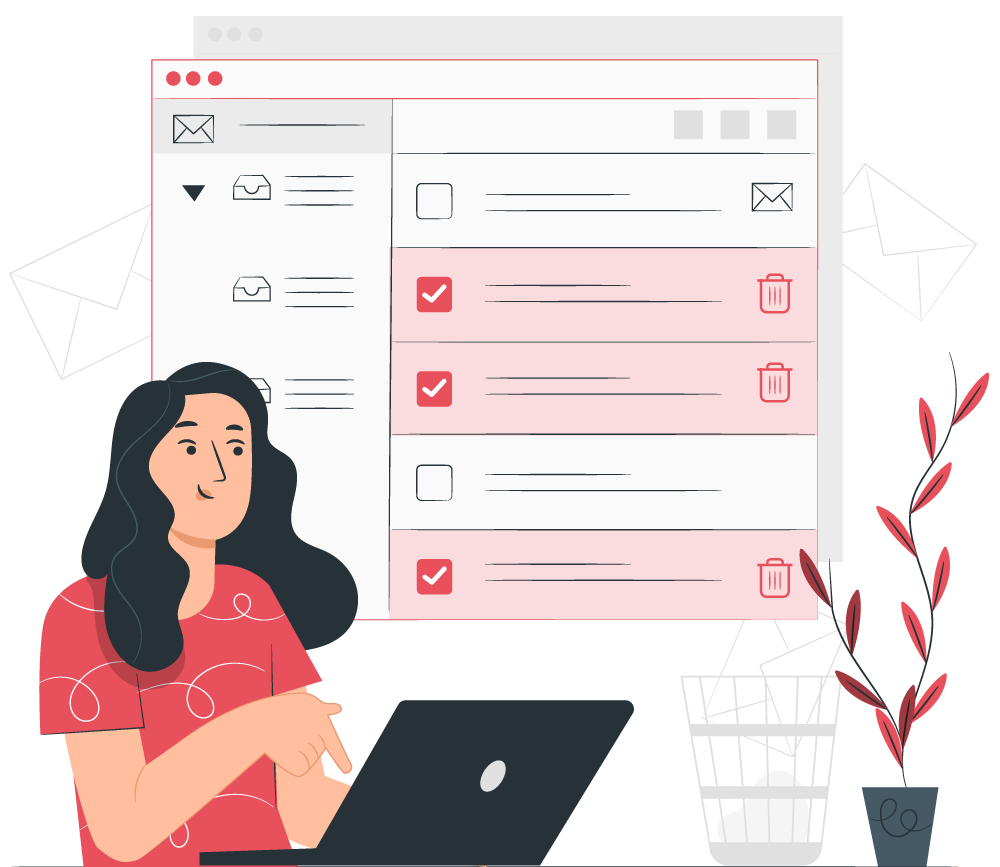
With NAT SECURITY FOR MAIL you can find the different types of emails placed in quarantine, applying filters according to the type of detection that has existed, which may be: Malware, Spam, Expression, Extension, MIME Type, DLP, unscannable, among others. Also, you can easily configure your BlackList and WhiteList filters.

NAT SECURITY FOR MAIL works together with four RBL’s (Barracuda, Spamhaus, SpamCop and DNSBL) which work as a mail filter before it reaches its destination. Having as its main function, detecting which IP’s or domains are considered as possible threats.

You can hire this service depending on the system you have in your organization. If it is a cloud mail service such as Office 365, Kerio or Google (gsuite) then you can contract NAT SECURITY FOR MAIL – CLOUD. While, if you have a local mail server, then you can contract NAT SECURITY FOR MAIL – LOCAL, NAT being in charge of providing you with the security device which is included in the contracting price of this service.

NAT SECURITY FOR MAIL has various types of control for the emails we receive, these being: Content control, Expression control, Character control, word blocking, filters by extensions, file verification, sender identity verification, among others. It will have 20 GB of space, where these emails that have been detected as malicious or spam will be stored and these emails are deleted every 30, 60 or 90 days. In case the storage fills up before the set time, the system automatically frees up space.
New-Age Technology data centers are equipped with backup uninterruptible power supplies (UPS) and diesel generators, and are designed to ensure constant power availability for up to 48 hours during an indefinite power outage. In addition, there are redundant heating, ventilation and air conditioning (HVAC) systems, networks and UPS. Physical security is ensured through the use of high fences, 24/7 security personnel, and video surveillance with 90-day archiving. To access it is necessary to pass a biometric scan of the geometry of the hand and present a proximity card.
We have never really had problems with service outages, however, to ensure the Business Continuity of our clients, all our nodes are connected in an optical ring. The information is replicated to the next fastest responding DC in less than 15 minutes and everything continues as normal. We have our own nodes:AMÉRICAS: Washington (USA), New York (USA), Chicago (USA), Metro Kanzas (USA).
EUROPA: París (France).
PAISES BAJOS: Amsterdam.
ALEMANIA: Frankfurt am Main, Metro Karlsruhe , Munich.
To arrive at this answer, we must first mention that Backup tasks can be performed hot (working hours) or cold (non-working hours). Obviously it is more advisable to do it outside working hours so that it does not consume the bandwidth that users are surely using. In any case, if it is required to run the Backup hot, for example, because the Manager only works until noon and I need to backup his laptop before he leaves; In this case, we can assign a specific bandwidth to the task, thus avoiding saturated upload consumption (Post, Drive, online collaboration tools, etc.)
The data is stored encrypted in AES-256bits, which means that only the client with a username and password can access the information stored in our Cloud. You don’t need to be physically on your LAN to manage your backups: the console is 100% Cloud. We have privacy and confidentiality clauses with their respective penalties in accordance with the data protection law (DLP).
© 2022, New-Age Technology Inc. All rights reserved
























UN ASESOR COMERCIAL SE COMUNICARÁ A LA BREVEDAD CON USTED
